This is the 8th part of my Key Vault series - This time it has come to Azure DevOps. At Umbraco we've moved all of our build and release pipelines into Azure DevOps, this also forced us to look at how to get secrets from Key Vault, in order to do deployments and config transforms during pipeline executions.
When in Azure DevOps, use the Azure Key Vault Task
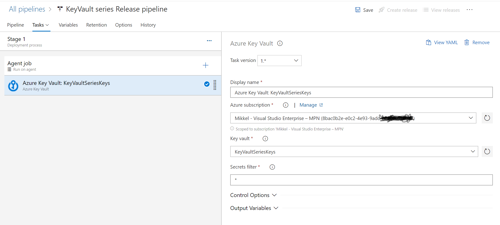
The Azure DevOps interface keeps evolving, and of this writing the build pipelines are in yaml, while the release pipelines are still in a "UI drag & drop"-kinda interface, so eventhough the task to implement is the same, it will look and feel a bit different.
Build pipelines
The objective is to add a task of type Azure Key Vault - this task will read all secrets (or the specified ones) into system variables that can then be used through the build pipeline.
In the build pipelines, everything is handled via yaml. Adding tasks can be done either by their wizard or just by typing the informations needed. i.e. in my pipeline I get access to the task by adding this task definition:
- task: AzureKeyVault@1 inputs: azureSubscription: 'Mikkel - Visual Studio Enterprise – MPN (8bxcxx2x-e0x2-4ex3-9axc-bx5x6x5x1xxx)' KeyVaultName: 'KeyVaultSeriesKeys' SecretsFilter: '*'
- script: echo Hello, world! $(MySuperSecretKey) displayName: 'Run a one-line script'
Release pipelines
- NuGet
- Octopus Deploy
- a Container Registry (like ACR)
- a Docker Engine
- a Kubernetes Cluster (like AKS)
- a Webapp via MSDeploy
- or simply copy them to a blob location
The credentials needed to access the destination, should all be stored in the Azure Key Vault instance, and then used when deploying. This should ensure that you only manage your secrets from one place, and that noone actually gets to see them, except the ones in charge of maintaining your Azure Key Vault.
